VLAN or set up a router with only one network card
I have often reported on Firewall Mini PCs here on the blog, which usually have 4 or even more network connections in order to separate networks with a firewall. But maybe there is another way.
Introduction

In a network, it is a good idea to separate different areas, such as WLAN, IoT devices and perhaps others, e.g. for guests, from each other in order to increase security. This is relatively easy to do with the firewall appliances offered by various manufacturers, including Amazon.
These have 4 or more network connections, a smaller Intel CPU and space for a drive on which you can install the operating system, e.g. Proxmox or directly an OPNSense or PFSense.
But is such a separation of the networks possible with just one physical network card? To say it up front, yes, it is possible with VLAN.
VLAN
VLAN or virtual LAN are a software solution for sending multiple network connections over a physical interface and just one cable. This can be done quite well either in Proxmox or OPNSense. I decided to go with the Proxmox route.
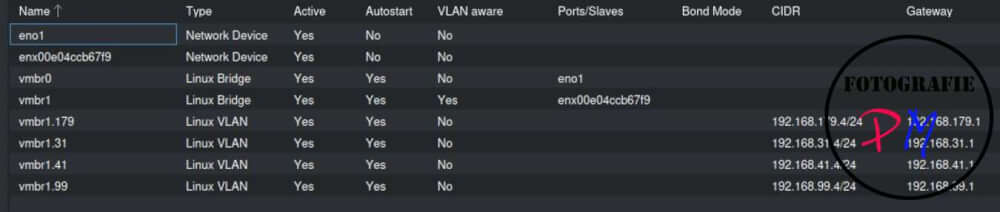
I have created a physical interface (see vmbr1) with multiple VLANs that take the VLAN TAG with them. In this case, you can create a network 31, 41 and 179. You can do this either in the GUI or by editing /etc/network/interfaces.
Firewall
The virtual network interfaces created in Proxmox arrive in the firewall as physical interfaces that can be assigned to the various areas.
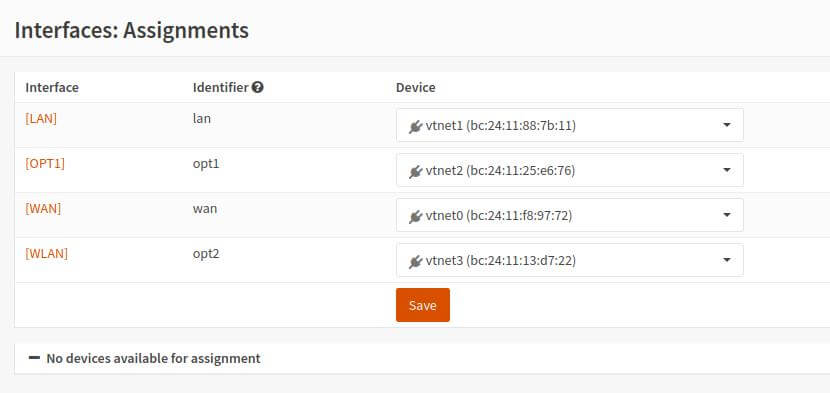
The Server

I installed this on my Asrock Deskmini H470 as a test. This PC only has a 1GB interface. In order to separate the internal networks on one side and the Internet on the other, I decided to create the WAN connection with the 1 GB interface and to create the other networks with an additional USB Ethernet interface.
This means that the PC only has the USB Ethernet adapter available to physically separate the different networks, which then has to distribute the network traffic in the internal networks.
But the Proxmox server cannot do this on its own, despite the fact that several VLANs have already been created here via virtual network interfaces.
The managed Switch
For the whole thing to work, you have to connect a switch that also supports VLAN. These are usually managed switches. These are available for around €30 for the 1 GB range, depending on the number of ports.
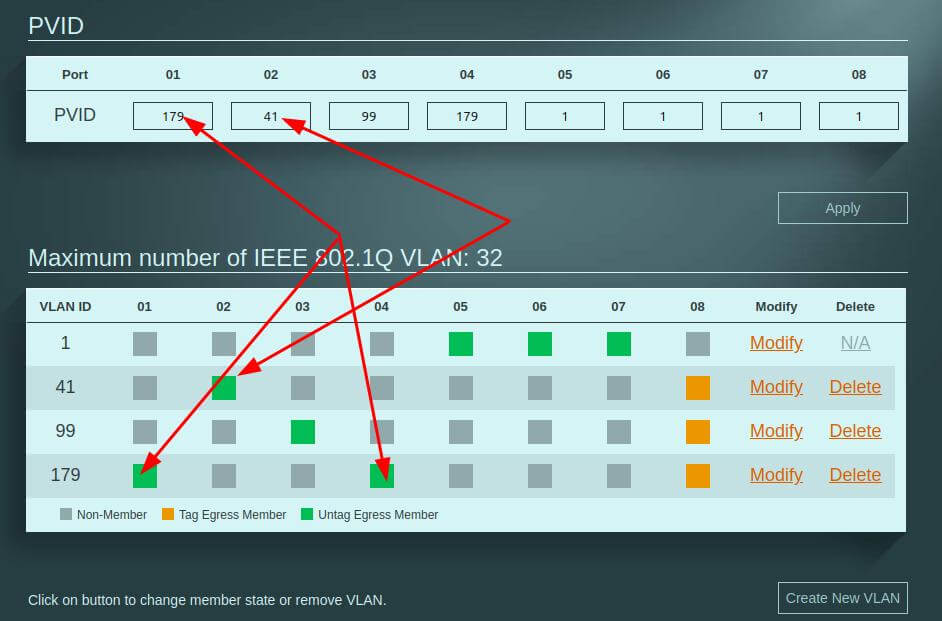
Here is an example of the Zyksel switch (every switch manufacturer may implement this slightly differently). VLAN 179 comes to port 1, VLAN 41 to port 2 and VLAN 99 to port 3. All of these ports pass the VLAN TAG, which is passed on via the PVID (top line) and the switch then knows where to send the packets, since the port handles all 3 VLANs.
The orange color means that the VLAN tag is passed on, in this case to the VLAN Aware Bridges within Proxmox and then to the OPNSense firewall. There, the firewall rules can be used to specify which network can connect to where.
In reality, they look like the picture above. All VLANs arrive at port 8, regardless of whether they originate from port 1 (VLAN 179) or port 2 (VLAN 41), for example.
Conclusion
VLANs are simply brilliant because they allow networks to be logically separated, even across physical network interfaces. This allows you to do more for your network security, even without having the number of network ports you might need.
ciao tuxoche



